Remote Access Trojan Techniques for prevention, inspection and disposal
Reviewjingjung สิงหาคม 13, 2019
What is a Remote Access Trojan? Techniques for prevention, inspection and disposal
Remote Access Trojans (RAT) have shown that Is the greatest risk of this world When talking about computer theft Or just prank with friends
RAT is classified as malicious software that allows the operator to control it Able to attack the computer And access from a remote location (without permission)
RAT has been there for many years. And we would like to confirm that finding some of the RATs is a difficult task for every modern Antivirus software.

In this post, we will see what is the Remote Access Trojan and talk about detection and removal techniques. About some features of common RATs such as CyberGate, DarkComet, Optix, Shark, Havex, ComRat, VorteX Rat, Sakula and KjW0rm รีวิว Assassin’s Creed Origins เกมส์โลกเปิดในตำนาน
Trojan is ?
For Remote Access Trojan, most will find a lot of malicious email downloads. Unauthorized programs And a web link that will take you anywhere
RAT’s behavior is not as easy to find as Keylogger.
Key locker
Your keystrokes Can check Especially the user name, password and other sensitive information Can recover Or steal some information
Screen capture
Can take screenshots To see what happens to your computer
Hardware caching from your device
RATs can access the webcam. And your microphone To save your video And your environment totally Which is a violation of the privacy that is extremely shocking
Administrator rights
The attacker may change the settings. Edit registry values And doing things More on your computer Without permission from you. RAT can grant administrator privileges to attackers
System overclocking
An attacker may increase your processor speed. Overclocking the system may harm the hardware components and eventually the hardware that runs over its load for a long time. Will burn himself to ashes in the end
Specific capabilities of other systems
The attacker can access various things On your computer, whether it be files, passwords, chat information and anything
How do Remote Access Trojans work?
Remote Access Trojans are server configurations – clients that install servers secretly. On the victim’s device and the client can use it to access the victim device via the GUI or command interface
The link between servers and the client is open on a specific port And encrypted communication Or normal Can occur between the server and the client
If the network and packets sent/received are checked properly Can specify and delete RATs
Preventing Trojan virus attacks

1. Install anti-virus software
RATs will find a way to the computer from junk mail, software that installs programs that aim to harm. Or caused by a combination of software Or other applications You need to have a good antivirus program. Installed on your computer Which can detect and eliminate RAT as well
Detecting RATs is quite difficult. Because it is installed under the use of random names Which may seem like other general applications So you need a really good antivirus program. To protect them
2. Check your network
Checking your network It may be a good way to detect Trojans that send your personal information over the internet.
If you do not use the remote administration tool Disable the remote assistance connection to your computer. You will be set in SystemProperties> Remote tab> Cancel Allowing Remote Assistance connections to this computer
3. Keep your system and applications updated
Update operating system, installed software And special security software at all times Also, try not to click emails that you don’t know and come from unreliable sources. Do not download any software from sources other than official websites or mirror sites.
What to do after getting RAT attacks?
1. Install antivirus software and perform a full scan immediately.
Scan the computer to check for problems. And ask for help from experts to remove the RAT. Consider using professional anti-virus software.
2. Change all passwords
When we know that it has been attacked The first step is to disconnect your system from the internet. And network if you connect Change all your passwords and other sensitive information And check that any account You being compromised Using a new computer, safe, etc.
3. Check your bank account
Check your bank account for transactions that are impersonating. And may notify the bank that you have used the service About Trojans on your computer immediately
General Remote Access Trojans
Many RATs are currently working. And causing millions of devices to be stuck We will mention the most famous RAT in this article:
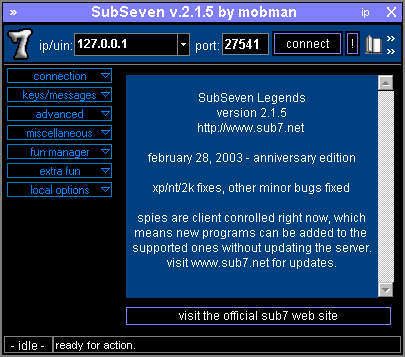
1. Sub 7
7 Sub7 ’is derived from the spelling of NetBus (the previous version of RAT). In the past Is a free remote administration tool that allows you to control the host device This tool is classified as a Trojan by security experts. And there may be a risk to have on your computer
More information from Wikipedia
2. Back Orifice
Back Orifice and the Back Orifice 2000 successor are the original free tools. That is for remote administration – but in no time It became a Remote Access Trojan. There is a dispute that this tool is a Trojan. But software developers agreed with the fact that It is a legitimate tool. That provides remote access to system administration This program has been identified as malware by most antivirus software.
More information from Wikipedia
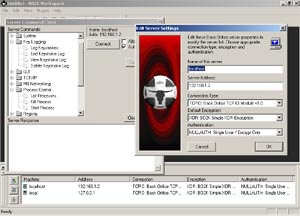
3. DarkComet
It is a remote administration tool that can be expanded and many features can be used to spy This tool is also linked to the Syrian civil war. Which is reported that the government uses this tool to spy on civilians.
This tool is used in many wrong ways. And the developer has stopped development
More information from Wikipedia

4. Havex
This Trojan is widely used in the industrial sector.
Have data collection behavior And then pass on the same information to the target website of the malicious person from a distance
More information from Wikipedia
5. KjW0rm
This trojan comes with many abilities. But was marked as a threat by many antivirus tools
conclusion
This Remote Access Trojan allows many hackers to exploit millions of computers that are victims.
Need to protect these tools and have a good safety program With user notification To protect these Trojans from your computer
This article is intended to be an article that provides information about RAT and does not promote its use in any way.
There may be some laws regarding the use of such tools in your country. In any case








